The Problem
In 2013, assessing the security of Android applications still involves a lot of manual, time-consuming tasks - especially when performing a black-box assessment. Without access to source code, a comprehensive review of these application currently requires in-depth knowledge of various APIs and the ability to use generic tools or just jump straight into the debugger.
To simplify this process, we are releasing Introspy-Android - an open-source security profiler for Android. Introspy is designed to help penetration testers understand what an application does at runtime.
How Introspy works
Introspy-Android comprises two separate components: a GUI interface to configure hooks, filters and options and a Cydia Substrate extension containing the core of the tool functionalities, including hooks and analysis of potential issues.
Introspy-Android can be installed on a rooted device and dynamically configured to hook security-sensitive Android APIs at run-time. The tool records all the relevant API calls made by an application, including function calls, arguments and return values. It then perform tests for security issues in real time and persists the results in a database and in the Android logging system.
The Introspy analyzer can then be used to analyze a database generated by the tracer, and generate HTML reports containing the list of logged function calls as well as a list of potential vulnerabilities affecting the application.
Tracer/Analyzer
Once installed, the tool will store in a SQLite database (and in the system logs) calls made by Android applications to security-sensitive APIs as well as potential issues.
Example of data dumped in logcat:
 cydia_installed
cydia_installed
Example of an HTML report (leveraging the Analyzer):
The GUI lets the user choose which Android App should be monitored and which APIs to monitor. The "NO DB" option disables logging into a database (which makes the apps faster) and the "STACK TRACE" option will save and log a minimal call stack for the selected filters.

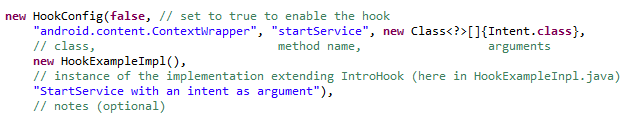
Easy way to add hooks
The tool was designed to make it easy for anyone to add hooks. To do so, you need to create a HookConfig object in CustomHookList.java (com.introspy.custom_hooks) as well as a call handler class in the same package. This class should extend IntroHook and implement an execute() method (see readme for more details).
Example:
Another example of an implementation for a PBKDF function:
Getting started
Instructions are available in the project's README on Introspy's Github repo.
Author
Marc Blanchou - @mblanchou