The Problem
In 2013, assessing the security of iOS applications still involves a lot of manual, time-consuming tasks - especially when performing a black-box assessment. Without access to source code, a comprehensive review of these application currently requires in-depth knowledge of various APIs and the ability to use relatively complex, generic tools such as Cycript, or Mobile Substrate - or just jump straight into the debugger.
To simplify this process, we are releasing Introspy - an open-source security profiler for iOS. Introspy is designed to help penetration testers understand what an application does at runtime.
How Introspy works
The tool comprises two separate components: Introspy-iOS and Introspy-Analyzer.
Introspy-iOS is a tracer that can be installed on a jailbroken iOS device. It will hook security-sensitive APIs called by a given application, including functions related to cryptography, IPCs, data storage / protection, networking, and user privacy. The call details are all recorded and persisted in a SQLite database on the device
This database can then be fed to Introspy-Analyzer, which generates an HTML report displaying all recorded calls, plus a list of potential vulnerabilities affecting the application.
Tracer
Once installed, Introspy-iOS will store in a SQLite database all calls made by iOS applications to security-sensitive APIs.
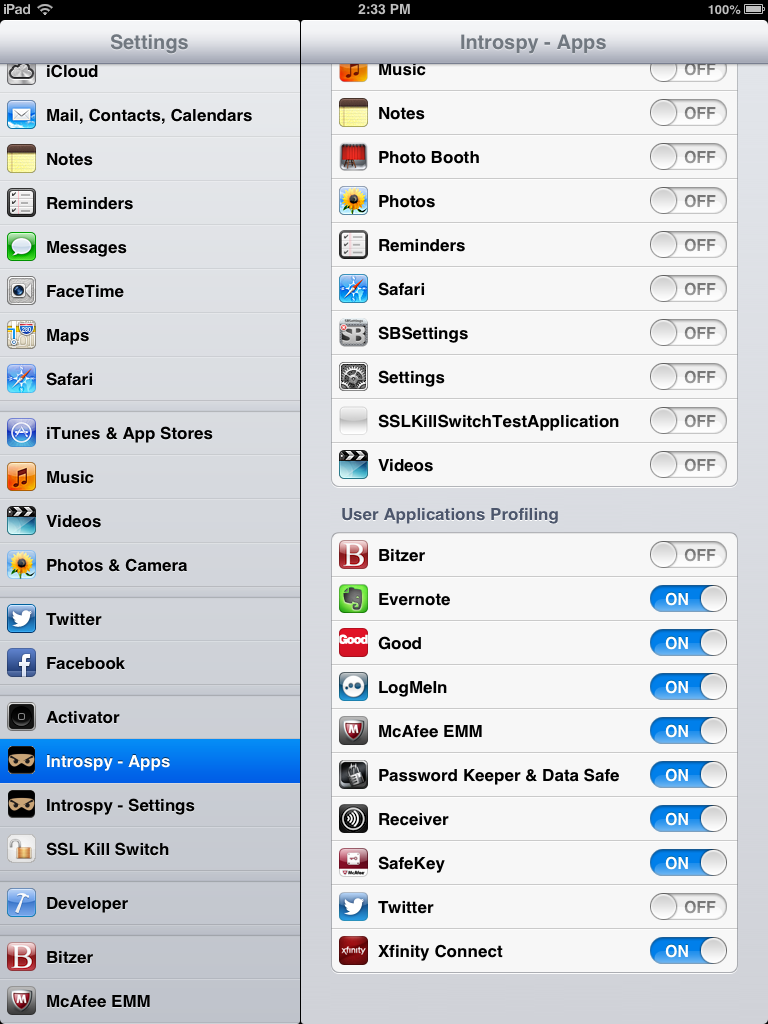
Selecting Apps to be monitored
Introspy-iOS lets the user choose which iOS App should be monitored:
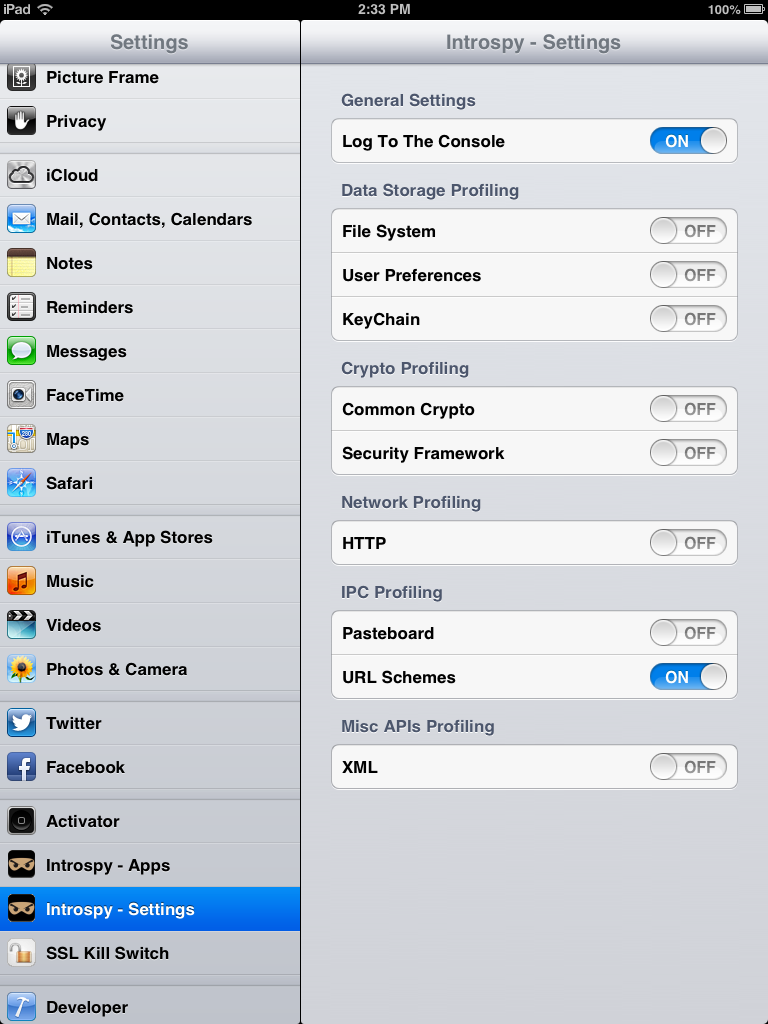
Selecting APIs to be profiled
Introspy-iOS lets the user choose which APIs should be recorded:
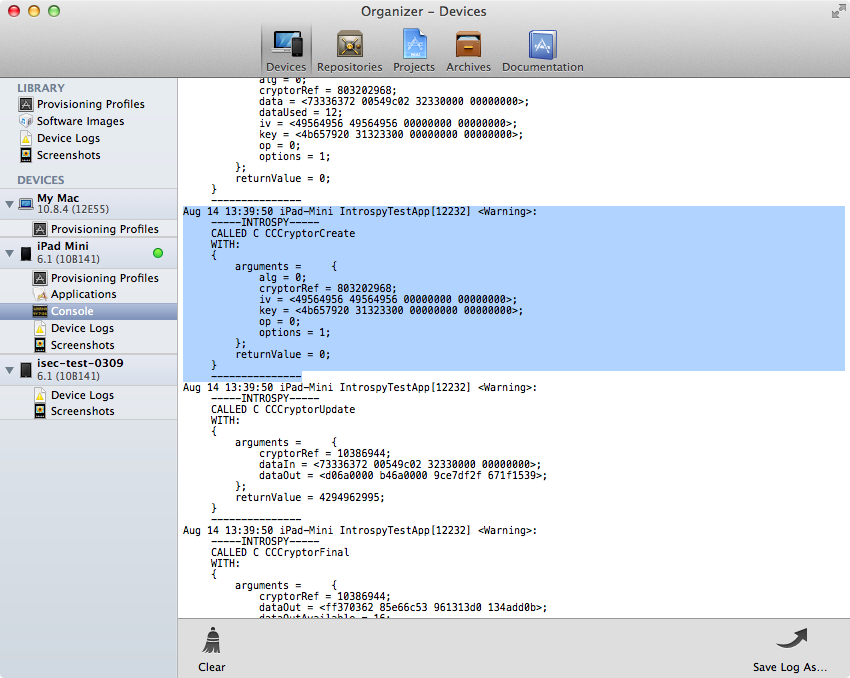
Logging to the console
Introspy-iOS can be configured to log all profiled calls to the console in real time:
Introspy-Analyzer
Introspy-Analyzer is a Python script that can process a SQLite database generated by the tracer and output various information about the traced calls or generate an HTML report. It is hosted on a separate GitHub repository.
Recovering a SQLite DB from an iOS device
The analyzer can connect to a device over SSH and recover DB files generated by the tracer:
$ python introspy.py -p ios --outdir e-bank -f 192.168.1.127
mobile@192.168.1.127's password:
0. ./Applications/94656731-0259-4AE9-9EEE-BADC9244AD82/introspy-com.isecpartners.e-bank.db
1. ./introspy-com.apple.mobilemail.db
2. ./introspy-com.isecpartners.introspytestapp.db
Select the database to analyze: 0
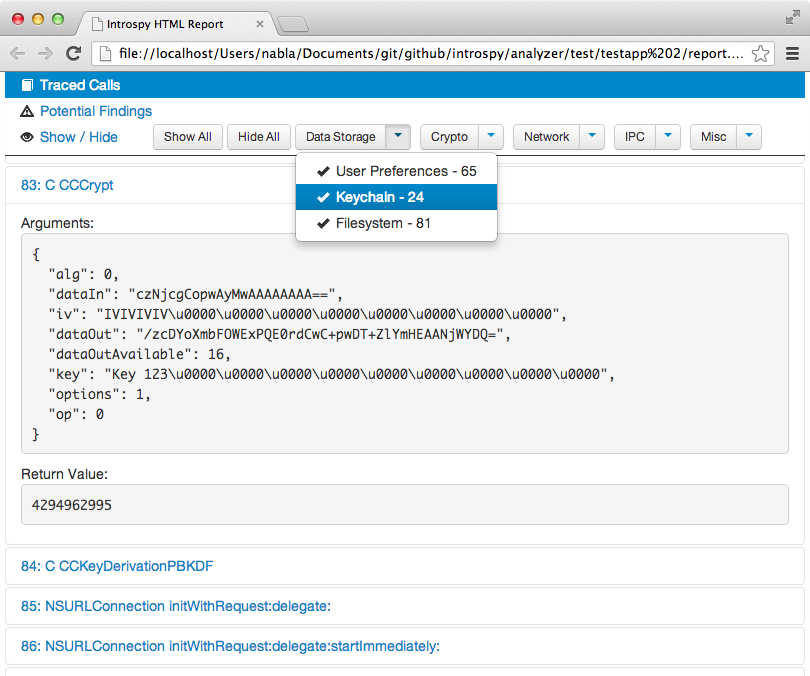
HTML Report - Traced calls
The analyzer can generate HTML reports displaying the list of all traced calls, including arguments and return values:
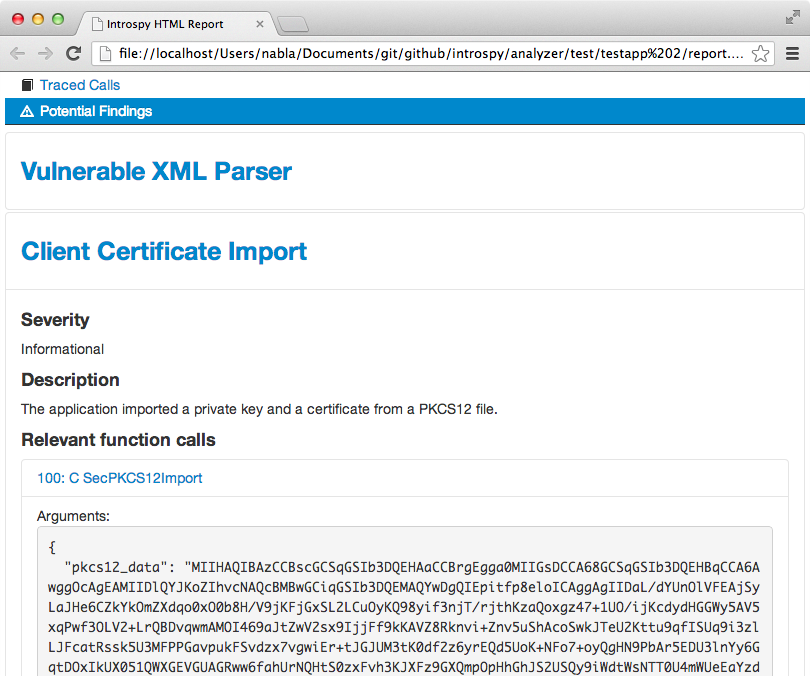
HTML Report - Potential findings
The analyzer will also explicitly flag potentially dangerous or interesting function calls:
Getting started
Instructions are available in the project's README on Introspy-iOS's Github repo.
Android
Introspy is also available for Android.
Authors
- Tom Daniels - @thirstscolr
- Alban Diquet - @nabla-c0d3